AnonSurf will anonymize the entire system under TOR using IPtables. It’s very easy to configure and possibly less hassle than setting up a VPN. Of course you will have slower connection speed than VPN as you are using TOR network.
Anonsurf works in the background (you can close the terminal), and changes ip address automatically every few minutes.
NOTE: DO NOT run this as
service anonsurf $COMMAND. Run this as
anonsurf $COMMAND 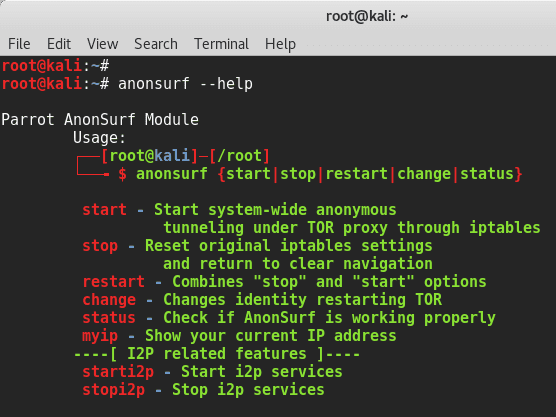
Download Anonsurf:
Clone anonsurf from GIT
root@kali:~# git clone https://github.com/Und3rf10w/kali-anonsurf Cloning into 'kali-anonsurf'... remote: Counting objects: 275, done. remote: Total 275 (delta 0), reused 0 (delta 0), pack-reused 275 Receiving objects: 100% (275/275), 163.44 KiB | 75.00 KiB/s, done. Resolving deltas: 100% (79/79), done. Checking connectivity... done.
root@kali:~# cd anonsurf/ root@kali:~/anonsurf# root@kali:~/anonsurf# ls installer.sh anonsurf-deb-src LICENSE README.md root@kali:~/anonsurf#
Install anonsurf:
With the installer script, it’s very straight forward to install anonsurf in Kali Linux.root@kali:~/kali-anonsurf# ./installer.sh --2016-10-13 12:36:53-- https://geti2p.net/ Resolving geti2p.net (geti2p.net)... 2a02:180:a:65 Connecting to geti2p.net (geti2p.net)|2a02:180:a:65 connected. HTTP request sent, awaiting response... 200 OK Length: 14455 (14K) [text/plain] Saving to: ‘/tmp/i2p-debian-repo.key.asc’ /tmp/i2p-debian-rep 100%[===================>] 14.12K 21.6KB/s in 0.7s <--------output-----truncated------->
It also changes your resolver configuration to the following:
root@kali:~# cat /etc/resolv.conf nameserver 127.0.0.1 nameserver 209.222.18.222 nameserver 209.222.18.218
Start anonsurf:
To start anonsurf, and pass all under TOR, simply start anonsurf. It will also start TOR if that already been started:
root@kali:~# anonsurf start * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping IPv6 services: [ i ] Starting anonymous mode: * Tor is not running! starting it for you * Saved iptables rules * Modified resolv.conf to use Tor and Private Internet Access DNS * All traffic was redirected throught Tor [ i ] You are under AnonSurf tunnel
Find your new Public IP:
You can issue the following command to find out your IP adderss
root@kali:~# anonsurf myip My ip is: 1xx.1xx.2xx.1xx
Restart anonsurf:
If you want a new IP address, simply restart anonsurf:
root@kali:~# anonsurf restart * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping anonymous mode: * Deleted all iptables rules * Iptables rules restored [ i ] Reenabling IPv6 services: * Anonymous mode stopped * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping IPv6 services: [ i ] Starting anonymous mode: * Tor is not running! starting it for you * Saved iptables rules * Modified resolv.conf to use Tor and Private Internet Access DNS * All traffic was redirected throught Tor [ i ] You are under AnonSurf tunnel
Stop anonsurf :
To stop anonsurf,
root@kali:~# anonsurf stop * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping anonymous mode: * Deleted all iptables rules * Iptables rules restored [ i ] Reenabling IPv6 services: * Anonymous mode stopped
Conclusion:
Those who doesn’t know what ParrotSec OS is, it is another Security OS similar to Kali Linux developed by Parrot Security.
In case ip spoofing in Kali Linux is a requirement for you, try torsocks. It uses SOCKS proxy which is not commonly used, so chances are you will have fast browsing experiences compared to standard TOR settings.
Stay tuned for more info....



![postgresql selected, no connection error [!] - Metasploit](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgQKS0oDDpFb_0XZiUdvscT1fUEBlxfFy7IBVyBrEPxZ6Ad4UK_pZIt_al8104FEqQfsRkrn5S7mI5JvzqpigcMr6qqkctzsuJiFREhHVSvlIkQf7low2AIAUfcPyVtY1fkmnx-_ZgZLls/s72-c/2ENTk2K2.png)




![postgresql selected, no connection error [!] - Metasploit](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgQKS0oDDpFb_0XZiUdvscT1fUEBlxfFy7IBVyBrEPxZ6Ad4UK_pZIt_al8104FEqQfsRkrn5S7mI5JvzqpigcMr6qqkctzsuJiFREhHVSvlIkQf7low2AIAUfcPyVtY1fkmnx-_ZgZLls/w72-h72-p-k-no-nu/2ENTk2K2.png)

No comments:
Post a Comment